Why child of a scientist doesn’t always become a scientist

“Greatness is not a function of circumstance.
Greatness, it turns out, is largely a matter of conscious choice”
—Jim Collins, Good to Great
“It is a rough road that leads to the heights of greatness”
— Seneca
When I was in class 12th, our Physics teacher was like a scientist. So we named him Mr. Scientist. Every student loved him from heart. He was always got first rank and gold medallist in his entire education career. Because of his high level of concept delivery method, we could not understand his teachings properly.
I had an impression that, though we didn’t understand and couldn’t follow his teachings properly, his son must be as like him and definitely a great student.
One day I came to know that his son failed in 12th science exam last year.
I was shocked. How come son of Mr. Scientist could fail in 12th examination?
That question was stuck in my mind for long time. I started observing successful, intelligent people and compare their children with them as and when I get a chance to do so.
I started looking to know about the children of great scientist like Sir Einstein, Thomas Alva Edison and many more. Their children may be in good position in their lives but still not as famous or successful as their father or mother.
I concluded one thing after so many years of observation that:
Success is not always related to heredity.
Definition of Success is different from person to person. Success for one person may be to get a Job, for another person may be a great family. Some others may be to have own company, for some may be millionaire or billionaire. So everyone has his/her own success definition and success story.
But here I am talking about success in simple term, a reputed position in a society, to understand the topic easily.
After my conclusion that Success is not always related to heredity, I started searching for what is the reason why a scientist’s children do not always become scientist. Likewise a Doctor’s children do not always become doctor; IAS’s children do not always an IAS, a great business man’s children do not always a great businessman.
Even the reverse is also possible. We have seen many good news about becoming IAS officers and doctors and Engineers, and successful business person whose parents have nothing. Even their parents may not even seen school in their life time. They are self-made successful men or women.
I researched; I read so many books on success, attitude and topics related to success.
Finally I concluded one thing:
Success is all depends on Your Intension and Dedication.
Intension is your primary source of all your achievements in life. All universal forces will work and support you towards your intension. Intension is your spirit, your emotions, your feelings, your beliefs. This works from inside out, not from outside in.
Dedication is your commitment to achieve your intension. Commitment means you are committed to achieve whatever is your desire without any excuses. If you have excuses, ready with you, then you are not committed. You are just interested.
Alan Brown first coach of John Assaraf asked this question to him, “Are you committed or interested in achieving a goal”.
If these two forces intension and dedication work together in harmony no one can stops you from achieving anything in your life.
This is the reason a scientist’s son/daughter doesn’t always become a scientist. Same is applicable for all other scenarios too.
Parents became successful because of their own intension and dedication. Children have their own intension and dedication. So success level of parents and children can’t always be of same level and not depends on heredity.
This video is for you. Click Here.
Thank You.
Pranab Hazarika
Why do we always remember our First kiss?

When I had my first kiss I felt like I had been shot through the heart with a bolt of energy.
You can forget your wife’s birthday or even your marriage day, but I am sure you still remember your first kiss. I am not talking about the date of your first kiss. I am talking about the felling of your first kiss.
You are smiling from inside now. Though you can’t express your feelings now in front of anybody else, but you are feeling ecstatic remembering your first kiss.
Yes, you can take a pause in reading and remember your first kiss with full of feelings.
Nothing to worry about your wife or husband. They can’t enter your brain to see about whom you are actually thinking. They won’t know that it was not him or she.
It was totally a different world and different person. But for you that HE or SHE may be your current spouse too.
So person to person feelings may vary, but everyone remembers his/her first kiss.
Now come to the main point. Why we can remember our first kiss, that day or person or situation easily.
This all related to your brain and hormones released by your brain. One hormone is called Dopamine. It is also named as “Happy Hormone”
So when you kissed for the first time Dopamine released in your brain for the first time for that sensation or feelings or happiness. So our whole body, mind experience that happiness for the first time. First time of anything good makes us happy. So this is true for all other good experiences too. You can remember easily all first day things which make you happy.
After that gradually that happy feeling start getting diluting as our mind and body both senses that releasing of happy hormones often and become used to it.
Game of our mind:
This is the game of our mind and emotions.
Brain is the organ of this mind and the cerebro-spinal system of nerves puts us in conscious communication with every part of the body. This system of nerves responses to every sensation of light, heat, odor, sound and taste.
So Dopamine, the happy hormone is one of the main reasons of our happy mode and remembering good memories easily.
Youtube video link is for you here.
Thank you for reading.
Pranab Hazarika
BE | MBA | PMP | IoT Certified (IIT Kharagpur)
.
15 Golden Points: Book-Millionaire Success Habits


Book Name: Millionaire Success Habits
Author: Deam Graziosi
15 Golden Points:
- It’s not where you start, it’s where you finish.
- Climbing up the ladder of success has little to do with luck and lot to do with the right habits and proper attitude.
- Successful people everywhere are doing: whether they are working for somebody else or working for themselves, they do whatever they do to the best of their ability, as if boss is watching them every minute of every day.
- Secrets of art of persuasion by communication with people by listening to them
- “Where the heck are you going?” Most people don’t have the answer of this question.
- “What’s crazy about today’s society: everybody is racing around “Ferrari brains” but no one has their GPS on”
- “When you take the time to look backward from the future in order to create where you want to go over the next year, you have done more than most of people who are stuck in place.”
- “The difference between successful people and unsuccessful people is that successful people do the things the unsuccessful people don’t want to do”.
- Successful people don’t just do things to get by or get through the day, but do things to achieve something.
- Get amazing at what you are already good at.
- Choose your circle that boost your energy rather than drain it.
- Become Hero of your own story. Leave past behind, create a new success story.
- To create confidence concentrate of 3 major areas:
Courage, commitment, and capabilities.
- Sales are everything. Either you are selling any product, your time, or may be your smile, gesture and a loving word.
- “Don’t be afraid to fail: rather, use failures as learning opportunities.
You can review your copy here: https://amzn.to/3NqDTym
Thank you for reading so far. You are important for me, please leave your footprint here:
How to get E1-KLM details in Ericsson BSC in Winfiol

4 Commands to get E1 details in winfiol
Any command for 2G, related to any BSC can be executed only after log in to BSC first.
After log in to BSC we can execute any command in that particular BSC.
To Log in any BSC :
Command: eaw BSC name;
Example: eaw RBSCHK2;
Now let’s see 4 commands which we can use to get details of E1, KLM in a BSC.
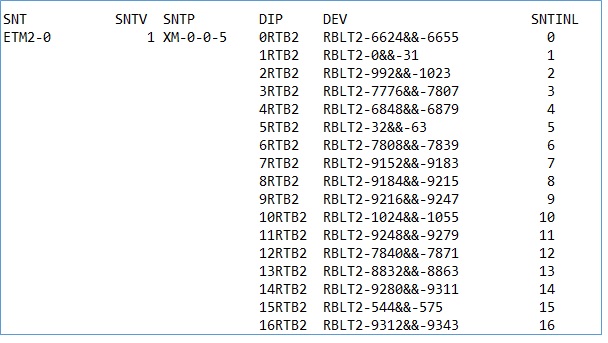
ntcop:snt=all;—————–E1 details/Device detail
The below screen shot is the output of the command ntcop:snt=all; .Through this command we can get STM wise details for each E1. In a single STM there are 63 E1s. Details of each E1 is available through this command. In the below mentioned screen shot ETM2-0 is the STM name. Then against each E1 DIP, Device (DEV) and SNTILN are mentioned. Against each SNTINL we get KLM details, e.g. KLM against SNTINL 1 is 211 and so on.
Likewise details for all available STMs in that same BSC can be extracted by using this ntcop:snt=all; command.
Here in each example, though I am showing only up to 16 E1 but through the command we will get details of all E1s. (for 1 STM 63 E1, and for all STMs available in the BSC)
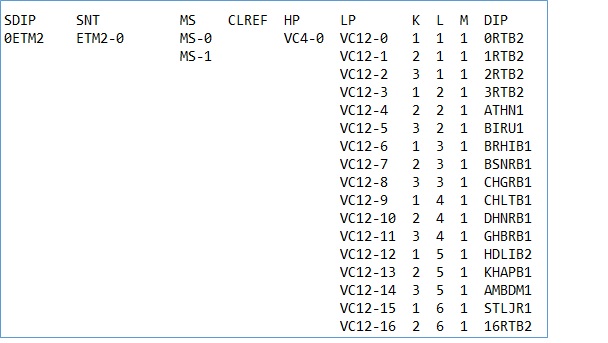
tpcop:sdip=all;——————-SNTINL details
By using tpcop:sdip=all; we can receive below mentioned details. Here also we get STM wise each E1 details for all STMs.
Don’t be confused with the screen shot of above command. Both data are for two different BSCs.
Here KLM actual value is indicated instead of SNTINL number. E.g. VC12-1 has KLM value 211, which represents SNTINL value 1. We don’t get device details through this command.
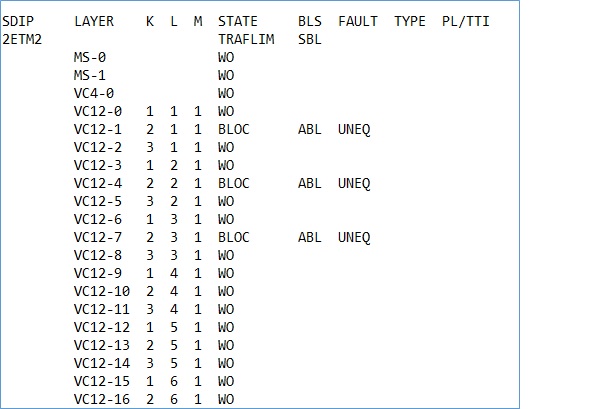
tpstp:sdip=all;—————-E1 status
tpstp:sdip=all; gives E1 status. Which E1 is currently busy/used and which are free. It gives details of each E1 KLM number wise for all STMs. If ABL is mentioned against some E1 then we can check those KLMs for free E1. They may not be free and can show ABL if site is down and currently not working.
So before using ABL mentioned E1, we have to check those KLMs properly.
If instead of ABL (Automatic blocked label), if MBL (Manually blocked label) is indicated against any E1/KLM then those E1 are manually blocked and currently free to use.
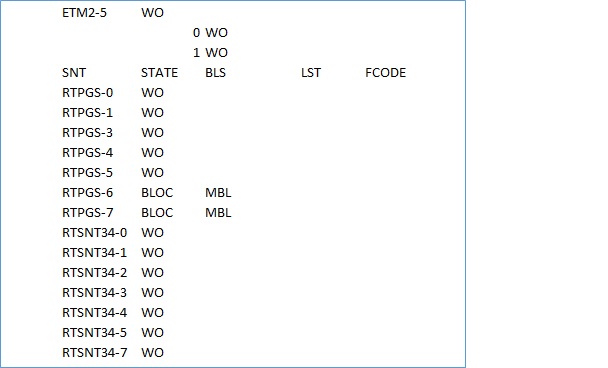
ntstp:snt=all;——————HW status
SNT wise, E1/KLM is currently used, or free can be seen by using ntstp:snt=all;
If we use above all three commands to get details of all E1s then we can avoid this command. This command will not give you details for all 63E1s of each STMs.
Conclusion:
These commands are useful to check which E1 are free. Free E1 we can use for site migration from one BSC to another BSC. During site migration we require to know free E1 along with DIP, KLM, attached device details and all. For those purpose these 4, especially top 3 commands are very useful.

Pranabjyoti Hazarika
BE | MBA | PMP | IoT-Certified
www.PranabHazarika.com
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-2754967439384345"
crossorigin="anonymous"></script>The PranabHazarika.com Privacy Policy
PranabHazarika (aka PranabHazarika.com) (“Company,” “we,” or “us”) respects your privacy and is committed to protecting it through this Privacy Policy.
This Privacy Policy governs your access to and use of PranabHazarika.com including any content, functionality and services offered on or through PranabHazarika.com (the “Website”), whether as a guest or a registered user.
When accessing the Website, we will learn certain information about you, both automatically and through voluntary actions you may take, during your visit. This policy applies to information we collect on the Website and in email, text, or other electronic messages between you and the Website.
Please read the Privacy Policy carefully before you start to use the Website.
Age of Consent
By using this site, you represent that you are at least the age of majority in your state or province of residence, or that you are the age of majority in your state or province of residence and you have given us your consent to allow any of your minor dependents to use this site.
PranabHazarika.com does not knowingly solicit or collect personally identifiable information online from children under the age of 13. If you become aware of any personally identifiable information we have collected from children under 13, please contact us and it will be removed.
Minors under 18 years of age may have the Personal Information that they provided through the site deleted by contacting us requesting deletion.
Information We Collect About You
When you access the Website, the Company will learn certain information about you during your visit. The Website provides various places for users to provide information. We collect information that users provide by filling out forms on the Website, communicating with us via contact forms, providing comments or other feedback, and providing information when ordering a product via the Website.
We use information you provide to us to provide the service and/or deliver the requested product, to improve our overall performance, and to provide you with offers, promotions, and information.
Information We Collect Through Automatic Data Collection Technology.
As you navigate through our Website, we may use automatic data collection technologies including Google Analytics to collect certain information about your equipment, browsing actions, and patterns. This will generally include information about your location, your traffic pattern through our website, and any communications between your computer and our Website. Among other things, we will collect data about the type of computer you use, your Internet connection, your IP address, your operating system, and your browser type.
The information we collect automatically is used for statistical data and will not include personal information. We use this data to improve our Website and our service offerings. To the extent that you voluntarily provide personal information to us, our systems will associate the automatically collected information with your personal information.
Use of Cookies And Pixels
Similar to other commercial websites, our website utilizes a standard technology called “cookies” and server logs to collect information about how our site is used. Information gathered through cookies and server logs may include the date and time of visits, the pages viewed, time spent at our site, and the websites visited just before and just after our own, as well as your IP address.
A cookie is a very small text document, which often includes an anonymous unique identifier. When you visit a website, that site’s computer asks your computer for permission to store this file in a part of your hard drive specifically designated for cookies. Each website can send its own cookie to your browser if your browser’s preferences allow it, but (to protect your privacy) your browser only permits a website to access the cookies it has already sent to you, not the cookies sent to you by other sites.
The Company reserves the right to use technological equivalents of cookies, including social media pixels. These pixels allow social media sites to track visitors to outside websites so as to tailor advertising messages users see while visiting that social media website. The Company reserves the right to use these pixels in compliance with the policies of the various social media sites.
PranabHazarika may use cookies and tracking technology which are useful for gathering information such as browser type and operating system, tracking the number of visitors to the site, and understanding how visitors use the Site. Personal information cannot be collected via cookies and other tracking technology, however, if you previously provided personally identifiable information, cookies may be tied to such information. Third parties such as our advertisers may also use cookies to collect information in the course of serving ads to you. Most web browsers automatically accept cookies, but you can usually modify your browser setting to decline cookies if you prefer. Google, in particular, as a third party vendor, uses cookies to serve ads on this site. Google’s use of the DART cookie enables it to serve ads to your users based on their visit to your sites and other sites on the Internet. Users may opt out of the use of the DART cookie by visiting the Google ad and content network privacy policy.
Third Party Use Of Cookies
Some content or applications, including advertisements, on the Website are served by third-parties, including advertisers, ad networks and servers, content providers, and application providers. These third parties may use cookies alone or in conjunction with web beacons or other tracking technologies to collect information about you when you use our website. The information they collect may be associated with your personal information or they may collect information, including personal information, about your online activities over time and across different websites and other online services. They may use this information to provide you with interest-based (behavioral) advertising or other targeted content.
We do not control these third parties’ tracking technologies or how they may be used. If you have any questions about an advertisement or other targeted content, you should contact the responsible provider directly.
International Transfer
Your information, including Personal Information, may be transferred to — and maintained on — computers located outside of your state, province, country or other governmental jurisdiction where the data protection laws may differ than those from your jurisdiction. If you are located outside United States and choose to provide information to us, please note that we transfer the information, including Personal Information, to the United States and process it there. Your consent to this Privacy Policy followed by your submission of such information represents your agreement to that transfer.
Links To Other Sites
Our Service may contain links to other sites that are not operated by us. If you click on a third party link, you will be directed to that third party’s site. We strongly advise you to review the Privacy Policy of every site you visit.
We have no control over, and assume no responsibility for the content, privacy policies or practices of any third party sites or services.
Comments
Comments submitted to this website are the responsibility of the commenter. We reserve the right to remove or edit comments at our discretion. Site URLs (if provided) are published along with comments. E-mail addresses are required with the submission of comments but are not disclosed, unless the commenter deliberately does so him/herself by entering the e-mail address in the main comment box in addition to the box clearly labeled for the e-mail address.
PranabHazarika reserves the right to delete any comments that it deems not beneficial to the readership. This includes but is not limited to comments containing profanity, self promotion, harassment, threats, or spam of any sort.
Email Information
If you choose to correspond with us through email, we may retain the content of your email messages together with your email address and our responses. We provide the same protections for these electronic communications that we employ in the maintenance of information received online, mail, and telephone. This also applies when you register for our website, sign up through any of our forms using your email address or make a purchase on this site. For further information see the email policies below.
Email Policies
We are committed to keeping your e-mail address confidential. We do not sell, rent, or lease our subscription lists to third parties, and will not disclose your email address to any third parties except as allowed in the section titled Disclosure of Your Information.
We will maintain the information you send via e-mail in accordance with applicable federal law.
In compliance with the CAN-SPAM Act, all e-mails sent from our organization will clearly state who the e-mail is from and provide clear information on how to contact the sender. In addition, all e-mail messages will also contain concise information on how to remove yourself from our mailing list so that you receive no further e-mail communication from us.
Our emails provide users the opportunity to opt-out of receiving communications from us and our partners by reading the unsubscribe instructions located at the bottom of any e-mail they receive from us at anytime.
Users who no longer wish to receive our newsletter or promotional materials may opt-out of receiving these communications by clicking on the unsubscribe link in the e-mail.
How And Why We Collect Information
The Company collects your information in order to record and support your participation in the activities you select. We use this information to track your preferences and to keep you informed about the products and services you have selected to receive and any related products and/or services. As a visitor to this Website, you can engage in most activities without providing any personal information. It is only when you seek to download resources and/or purchase products that you are required to provide information.
If you opt to receive any free resources, participate in any free training programs, register for a webinar, register for a live event, register for a seminar, or purchase any products sold by the Company on this Website, we will automatically enroll you to receive our email newsletter. If you do not wish to receive this communication, you can unsubscribe anytime. We include an “unsubscribe” link at the bottom of every email we send. If you ever have trouble unsubscribing, you can contact us here requesting to unsubscribe from future emails.
How Do We Use the Information That You Provide to Us?
We use personal information for purposes of presenting our Website and its contents to you, providing you with information, providing you with offers for products and services, providing you with information about your subscriptions and products, carrying out any contract between you and the Company, administering our business activities, providing customer service, and making available other items and services to our customers and prospective customers.
From time-to-time, we may use the information you provide to us to make you offers to purchase products and services provided by third parties in exchange for a commission to be paid to us by such third parties. Should you opt to take part in such promotions, the third parties will receive your information.
From time-to-time, we may use the information you provide to us to display advertisements to you that are tailored to your personal characteristics, interests, and activities.
Disclosure Of Your Information
As a general rule, we do not sell, rent, lease or otherwise transfer any information collected whether automatically or through your voluntary action.
We may disclose your personal information to our subsidiaries, affiliates, and service providers for the purpose of providing our services to you.
We may disclose your personal information to a third party, including a lawyer or collection agency, when necessary to enforce our terms of service or any other agreement between you and the Company.
We may disclose information when legally compelled to do so, in other words, when we, in good faith, believe that the law requires it or for the protection of our legal rights or when compelled by a court or other governmental entity to do so.
How Do We Protect Your Information and Secure Information Transmissions?
The security of your Personal Information is important to us, and we strive to implement and maintain reasonable, commercially acceptable security procedures and practices appropriate to the nature of the information we store, in order to protect it from unauthorized access, destruction, use, modification, or disclosure. However, please be aware that no method of transmission over the internet, or method of electronic storage is 100% secure and we are unable to guarantee the absolute security of the Personal Information we have collected from you.
We employ commercially reasonable methods to ensure the security of the information you provide to us and the information we collect automatically.
Email is not recognized as a secure medium of communication. For this reason, we request that you do not send private information to us by email. However, doing so is allowed, but at your own risk. Credit Card information and other sensitive information is never transmitted via email.
The Company may use software programs to create summary statistics, which are used for such purposes as assessing the number of visitors to our site, what information is of most and least interest, determining technical design specifications, and identifying system performance or problem areas.
For site security purposes and to ensure that this service remains available to all users, the Company uses software programs to monitor network traffic to identify unauthorized attempts to upload or change information, or otherwise cause damage.
Policy Changes
It is our policy to post any changes we make to our privacy policy on this page. If we make material changes to how we treat our users’ personal information, we will notify you by email to the email address specified in your account and/or through a notice on the Website home page. The date the privacy policy was last revised is identified at the bottom of the page. You are responsible for ensuring we have an up-to-date active and deliverable email address for you, and for periodically visiting our Website and this privacy policy to check for any changes.
Visitors’ GDPR Rights
If you are within the European Union, you are entitled to certain information and have certain rights under the General Data Protection Regulation. Those rights include:
We will retain the any information you choose to provide to us until the earlier of: (a) you asking us to delete the information, (b) our decision to cease using our existing data providers, or (c) the Company decides that the value in retaining the data is outweighed by the costs of retaining it.
- You have the right to request access to your data that the Company stores and the rights to either rectify or erase your personal data.
- You have the right to seek restrictions on the processing of your data.
- You have the right to object to the processing of your data and the right to the portability of your data.
- To exercise these rights please contact us here.
- To the extent that you provided consent to the Company’s processing of your personal data, you have the right to withdraw that consent at any time, without affecting the lawfulness of processing based upon consent that occurred prior to your withdrawal of consent.
- You have the right to lodge a complaint with a supervisory authority that has jurisdiction over issues related to the General Data Protection Regulation.
We require only the information that is reasonably required to enter into a contract with you. We will not require you to provide consent for any unnecessary processing as a condition of entering into a contract with us.
Contact Us
The Company welcomes your questions or comments regarding the Privacy Policy:
Mail: hazarikap@gmail.com
Last updated Dec’28, 2021
Copyright
Copyright © 2018 by PranabHazarika.
All Rights Reserved. No part of the content of this website may be reproduced, stored in a retrieval system (including but not limited to computers, disks, external drives, tapes, electronic or digital devices, e-readers, websites), or transmitted in any form or by any means ( including but not limited to cyclostyling, photocopying, docutech or other reprographic reproductions, mechanical, recording, electronic, digital versions) without the prior written permission of the publisher/creator PranabHazarika, nor be otherwise circulated in any form of binding or cover other than that in which it is reproduced and without a similar condition being imposed on the subsequent reader/purchaser.
Positive Learnings during COVID-19
How COVID-19 has impacted us

2012

When Hollywood movie 2012 was released in 2009, it was bit confusing that is really world is going to destroy in 2012.
After watching movie 2012, I felt like world will be like Hollywood zombie movies. Only very few human will left out and they will travel here and there and fight with each other for a piece of bread.
But we witnessed that it didn’t happen and we are in normal condition.
I thought 2012 was also a kind of most of the Hollywood movies where all the un-earthy destructive power reach earth and destroy NEW YORK CITY every time.
But why this Hollywood movie was made with name 2012 and showing all the destruction of this world. Why not 2013. Though most of us think that 13 is an unlucky number.
Sylvia Browne was a New York Times bestselling author and world famous psychic gave a hint to the 2012 in her famous book “Ends of Days”.
She narrated about two old cultural civilizations the Maya and Cherokee and how they related to 2012.
The Maya:

The Mayan Civilization is thought to have been born in the Yucatan Peninsula in about 2500 BC with a society of fifteen million people.
They excelled brilliantly in astronomy, hieroglyphic writing, science, mathematics, art, farming, weaving, architecture, and creating highly technical, intricate calendar system.
Mayan calendar which consisted of cycles of 264 days, each day having one of twenty names represented by its own symbol.
The Mayan calendar ends on December 21, 2012.
The Cherokee:

The Cherokee are an intensely spiritual civilization who believed that each morning humankind should give thanks to the creator, to mother earth and to all good things.
Many of their predictions had already come true:
e.g.:
1. A cobweb would be built across the world through which people would talk:
A few hundred years after this prophesy, telephone lines reached into virtually every corner of the globe.
2. The eagle would someday fly in the night and land on the moon.
In 1969 the safe arrival on the moon of the Apollo 11 spacecraft was announced
By astronaut Neil Armstrong to NASA control room with the simple words,
“The eagle has landed.”
These are only two examples. There are list of their prophesies which were come true already.
The Cherokee calendar system also ends in year 2012.
Needless to say, it’s no coincidence that the Cherokee and Mayan calendars end in year 2012.
So it may be expected that movie 2012 was made based on some these kind of indications.
But thanks to God that it didn’t happen like movie 2012 and we are still here.
Earth is safe:

The good news is Earth is safe.
The Holy Vedas are accepted as originally spoken by the Lord himself to Brahma, from within his heart. The principles of religion are laid down in the Vedas.
In the Holy Rig Veda it is saying that everything was started with heat.
Even moon was also has heat and part of the earth.
Afterwards moon has lost his all heat.
Now Sun is the source of all the heat. Sun, still retains a great deal of heat, but it is not so intense as it was in the beginning. However a time will come when the sun will cool down to darkness and no more fountain of light and heat in its plan.
At that time earth will become a mass of solid. no air, no lakes, no animal, no humankind, nothing.
That time according to Aryan calculations is 2,333,227,018 years distance.
Modern scientific findings have reaffirmed the statement of this Vedic declaration.
So now we are happy that at least Earth is not going to end so early. World is not going to end in its natural process now.
Current situation and Prophesy

Bill Gates:
A viral video of Bill gates from a TED talk show in 2015 he mentioned few noticeable points as below:
For Global Catastrophe-
Who is more harmful: Not Missiles but Micros, It is not war it is Virus.
We have invested a lot in nuclear deterrence but not in a system to stop epidemic that happened like in back 1918.
We are not ready for the next epidemic.
Corona Virus Prophesy by Sylvia Browne:

In the book “END of DAYS” Sylvia Browne, who was a physic from her age three, did the prediction about Corona virus as below:
“In around 2020 a severe pneumonia-like illness will spread throughout the globe, attacking the lungs and the bronchial tubes and resisting all known treatments. Almost more baffling than the illness itself will be the fact that it will suddenly vanish as quickly as it arrived, attack again ten years later, and then disappear completely.”
Shocking prophesy which came true and we are witnessing it now.
Knowledge is Power

We know knowledge is the power. If we don’t know something we need to educate ourselves.
What now Government and every doctor and experienced people are trying to spread their messages about how we can protect ourselves from Corona or any kind of information related to COVID19 which can be helpful for all of us.
During this lock down period, I watched a video of Dr.Biswaroop Roy Chowdhury.
He said in his video that Corona Virus may exists even before humankind. It may be here till the time earth was created. But we didn’t know about it till the time we have an advanced microscope to see it.
I have read Holy Vedas and after listening to his video I realized one thing,
We can’t think of knowledge by eliminating God from his creation. After all what is knowledge? What is Physics? Or metaphysics? It is not with reference to our great creation? It is just a little activity in the dynamic world in a particular parameter.
Vedic Theism is a concept of dynamic reality. The supreme reality is our concern every moment. We might ignore him, as we usually do, but he doesn’t neglect us.
“The cosmic energy is the generator of the Universe, the
Embryo of waters, the leader of humans, most virile defender of human race.
It remains ever illuminated by its own radiance and
It provides sustenance for its beloved progeny.
(Rig Veda. 3.1.12)
Mind Body relationship:
“In this creation are held in balance the three regions, terrestrial, interspatial and celestial, and the three divine realms pertaining to body, mind and spirit provided with three eternal functions- physical, mental and transcendental.”
(Rig Veda. 2.27.8)
Dr.Deepk Chopra (MD) serves as a clinical professor at the University of California, San Diego and author of 89 books, numerous New York Times bestsellers, in his book “Perfect Health-The complete mind body guide” said about the relationship between body and mind.
He said,how different emotions and anxiety can reduce our immunity power.
With stress and anxiety,stress hormone “cortisol” released by the adrenal glands, of our brain which reduces our immunity power.
If we are happy and have something interesting, and exciting brain releases “dopamine” the happy hormone, which is good for heath.
That’s why “laughing club” is becoming popular in recent days.
So in such scenarios we should try to be in control of our stress and anxiety.
“When you cannot
Control a situation…
You must learn to
Control yourself.”
Jhon Assaraf
That’s why now a day’s people are more inclined towards Yoga, meditations and mindfulness.
Yoga synchronizes mind body relationship and meditations and mindfulness not only relaxes your brain, it also exercises the brain’s ability to focus.
Fast Life becomes Slow

Our “Autopilot” mode is now become “Stop” mode.
Now a days instead of mindfulness we work with “mindlessness”.
Mindlessness is the state of being so preoccupied with the list of things we have to do that we realize we don’t remember how we got from point A to point B, like from home to office in a car.
This results irritable, rushed, emotionally unavailable, anxious and depressed.
We drive to our office 15Km, 20Km and reache office, without enjoying any beautiful moment in the whole route.
Our driving is controlled by our subconscious mind whereas our conscious mind is busy in thinking of reports, presentations, VC, about boss, what would he say and all.
Sometimes we are so “mindlessness” that even we don’t remember the taste of the Sabji (food) that we took in our breakfast, and the worst part is that sometimes we don’t even remember what was in breakfast.
Mindfulness, on the other hand, means developing the ability to tolerate that anxiety and tension without being swept away.
Neuroplasticity:
Our brain is made of “gray matter”, it is nothing but of a size of a dot
( –>.<– ) i.e. kind of grain of sand.
This dot size is actually made up of special nerve cells called neurons.
One such dot sized grain can contain as many as 100,000 of these neurons.
These 100,000 neurons communicate with one another by sending signals called synapses.
This is just about 1 dot. Like this in our brains we have billions of ‘dot” and trillions of connections.
So now we can imagine how complicated our brain is!
The repeating task makes repeating of same signalling paths and thus path becomes stronger and stronger day by day and finally become habit after 21 days/66 days (we are discussing about this next).
In simple language it is like follow the same route while walking on a green field over and over makes a distinct route that is easy to identify later.
These things are well described by John Assaraf in his book “Innercise” and by psychotherapist PhD Richard O’Connor in his book “Rewire”.
Habit formation:
Motivational speaker Robin Sharma said that as per new research of University College of London, habit creation needs 66 days continuous process to hardwire our brain to make it a habit and free our will power from that particular task.
They have divided these 66 days in 3 parts (each of approximately 20 days)
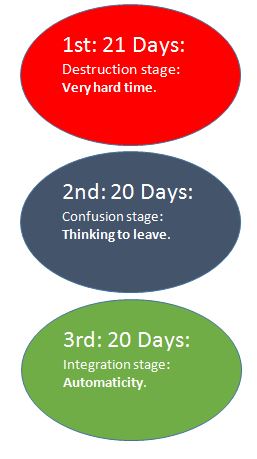
Still after reading many books on habit creation I found that new habit formation is wide-ranging from person to person based on his intention and interest and may vary from 4 to 90 days.
May be by seeing the science backed reason Indian Prime Minister Narendra Modi ji given a 21 days lock down so that after that it will become easy for us to stay at home for some more days if required.
MORE in Life:

More. We always want more. Even if we have accomplished all we have dreamed of or desired, perhaps we have noticed that there is a part of you that keeps nudging us toward whatever is next.
Sadhguru, the mystic says, every animal’s life ends two lines.
Ground line (Birth) and one upper line. In between these two lines their only thinking is to how to find food to serve their empty stomach.
But in case of human we have only one line i.e. ground line. There is no limit of the upper line. Our expectations, desires increases as we reach our milestones one by one.
BK Shivani of Brahmakuri says, “BUSY” word is a very dangerous word and once we start saying it, it drains down all our energy, like discharging of a mobile battery.
We fully charged our mobile battery before leaving for office or business.
But what about us. Our energy drained even after lunch period. Mindfulness is a way through which we can recharge ourselves after a periodic interval.
BK Shivani said this as “traffic control”.
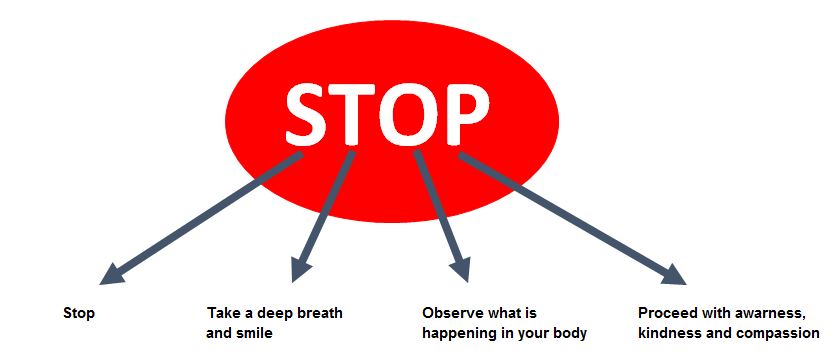
Dr. Deepak Chopra gives a way to calm and relax our mind at any moment is by doing STOP. STOP means:
Arianna Huffingtone, a member of Oprah’s Super Soul 100, is the co-founder, president and editor in chief of the Huffington Post Media Group, one of the world’s most influential news and information brands writes in her book “Thrive” how she had changed and start living her life from a frenetic to a well being life.
She taught us a very simple and the fastest way to achieve most of the things from our to-do list.
She gave example how she learned German language in just one day.
How…!!! She had a dream to learn German language and many more things to do in her life. These pending to-do list always push her in back of her mind and made an unknowing stress.
One day she realized that she can learn German by just deleting that task from her to do list.
Now she is mentally free and relaxed. Likewise she had completed many other task by deleting those from her to-do list.
I found it very interesting. Last year I joined in 3 different courses to upgrade myself with new technology like Artificial intelligence, Machine Learning and Internet of Things.
But I ended up with only one certificate. Removing other two subjects from my to-do list :).
4 Segments of Life:
Motivational speaker, writer Robin Sarma distinguished our life in 4 parts:
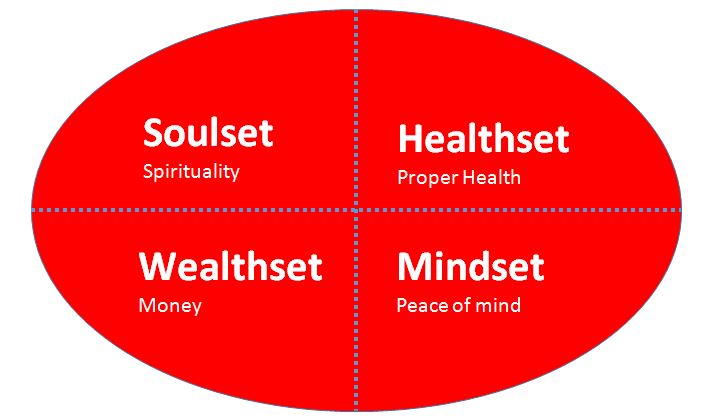
4 segments of life are interrelated. As we inclined more towards Wealthset, rest three get ignored most of the time.
In catastrophe we appreciated the importance of all of four. At that time we realize that Man-based religions are of a later date, whereas man’s natural religion is eternally with him.
Lessons Learned from COVID19
Gratitude:

Rhonda Byrne-The Secret, in her famous book “The Magic”, she has mentioned the power and magic of gratitude, the two powerful words “Thank You”
Albert Einstein who invented E=mc^2, said “Thank You” 100 times to this universe every day.
In these days gratitude automatically coming out from my heart.
These are some little thing, but sometimes the littlest things mean the most.
- I thank God every time before my each meal.
We usually said about our office canteen food, that foods are not tasty.
If today I will get that “Non-veg Thali” I will feel like having my lunch at a Five star Hotel.
- I thank God many times in a day, because of the fresh air, I breath.
Just imagine what could be the situation if CORONA spread through air and wind. At that scenario we can’t even think of to go to the lobby of our house.
- I thank God for water, to drink and for all necessary requirement.
- I thank God every day, for electricity supply, available at this time.
Now I feel importance of those things, which we usually taken for granted and complained many a times.
Some other learning are like:
- Cost of living to LIVE is not costly. Only spendthrift that we add to our lives make our life costly.
- Pollution control was almost like impossible in city like Delhi which is 21 of the world’s 30 most polluted city.
Delhi pollution reduced by 71% in just 7days from 91 to 26 micrograms per cubic meter of PM2.5.
So we have got a solution for pollution control in any city.
Nature’s Law:

There are two kinds of law.
- Men made law:e.g. Traffic signal
If we break man made law, we may or may not penalized.
2. Nature’s law:
If we break, we are definitely penalized.
Knowingly unknowingly everybody follow the laws of nature.
- Nature’s laws are equal for everyone.
- Same for under-developed, developing or developed country.
- Same for rich and poor.
- Independent of circumstances.
One example of Nature’s law is Death.
Controversy of China:

Many of us have already seen many controversial things related to Corona and China with different facts and figures.
This is all about China’s motive to become world’s economic power player.
As a normal person we can’t directly jump into a conclusion what is what.
COVID-19 may be a natural calamity or may be scientific result to gain control over the American and European companies operating in China, to become economic super power of the world.
In KALI YUGA it is said:
“Jugya Bhugya Basundhara”
Jugya: who is capable
Bhugya: who can enjoy life
Vasundhara: who has all the money and power.
It means in Kali Yuga, who has capability, he only can enjoy the life to its fullest and he will have all the money, fame and power.
Prophesy of New World

There is no such thing as typical prophet .God endows the gift of prophesy to a wide variety of people.
Here are some prophesies of our future new world.
Sir Isaac Newton:

Sir Isaac Newton the greatest mathematician was born on Christmas Day, 1642.
Apart from science, mathematics he wrote one book about Bible and published in 1727 after 6 years of his death named “Observations Upon the Prophecies of Daniel and Apocalypse of St. John”
There he mentioned that the year will be 2060. The date of the end of time, calculated from Biblical information by most brilliant mathematician in the world has ever known.
Edgar Cayce:

Edgar Cayce known as “The Sleeping Prophet” has the gift of prophesy while in a deep self-induced, trance like sleep, none of which he was able to recall when he was awake.
All his lifetime reading during his deep sleep converted into 300 books.
His prophesy said:
“As we prepare for the Second Coming of Christ, A new order of conditions is to arise. Then certain circumstances will arise in the political, the economic and a whole relationship to which a leaving will occur, or a greater comprehension of the need for it.
And then the deeds, the prayers of the faithful, will glorify the Father as peace and love will reign for those who love the Lord.”
Sir Isaac Newton has done this calculation mathematically and found this year would be 2060.
Bhagwat Geeta:

As per Hindusim the world goes through as part of ‘cycles of yugas’.
Four yogas are Satya, Treta, Dvaparaand Kali Yuga.
Kali Yuga started in 3102 BCE.
Madame Helena Blavatsky, Russian author was born in 1831 author of the book “The Secret doctrine” mentioned about the Kali Yuga as-
“We are at the close of the cycle of 5000 years of the present Aryan Kali Yuga or dark age. This will be succeeded by an age of light. This race will be altered in mentality and will move toward a more perfect spiritual existence.”
As in Geeta Lord Krishna said:
“Yada Yada hi Dharmasya
Glanir Bhavati Bharata
Abhyutthanam Adharmasya
Tadatmanam srja my Aham”
Whenever and wherever there is a decline and discrepancies in religious practices, a predominant rise of irreligion, and a disappearance of true religion,at that time Lord manifests himself and appear on earth to save the humankind from all negative power.
Tim LaHaye and Jerry Jenkins:
There is a series written by Tim LaHaye and Jerry Jenkins about Second coming of Christ has sold over sixty-five million copies, and the essential message is that the physical return of Jesus is quickly approaching.
Conclusion of Prophecies:

Prophesy is always a future event. We don’t have control over it. So we may accept with some past reference that some prophecies may come true and some will not.
So the passionate pursuit of the “truth” about the “end of days” is likely to be continued until the end of days itself. In Bible Jesus never mentioned anything like end of days.
It means world should never become the world like Zombies Hollywood movies.
There may be some revolution in terms of humanity, but world is going to have humankind till the time world itself decided to clean us from here.
Beauty of Life

“I’m afraid of dying, but I’m not afraid of death”
We know the Universal truth of death. So we never worry about death. But we always worry about the process of death.
Our life is just one second between past and future. Past is already gone, we don’t have any control over it. Future is what we don’t know.
If we think more about past then we feel sad, if we think more about future then we feel anxious.
So better live this day to its fullest and enjoy and see beauty of life everywhere.
“Mayest thou develop harmony with all
And enjoy life in full.
(Yajur Veda 7.5)
Pure Happiness:

In the end everyone knowingly or unknowingly wants only one thing:
Pure happiness with honest mind. Leaving behind all fear,anxiety, anger, resentment, envy and all negative energy things, and replace those with the Universe’s highest energy word i.e. LOVE and only LOVE.
This kind of purity of happy life we can enjoy in each and every day, by just changing our mind.
How you look at things changes the things you look at.
End
Now in such scenario Doctors and all medical fraternity are playing their roles like God. They are the savers. Thank you to them.
Thank you to all the scientist, researchers who are trying their best to develop some medicines/vaccine to stop this epidemic.
Let’s end up with two lines of Bob Marley’s famous song “One Love, one heart”
“Let’s get together
(everybody follow the rules, and stay at home ):)
To fight this Holy Armageddon,
So when the man comes
There will be no, no doom.”
Thank you. Thank You. Thank You.
With LOVE,

Pranab Hazarika
A Creative Engineer, Blogger by passion.
Disclaimer
I am not a Guru, motivational lecturer, public speaker, or anything else. I am a simple humble person with a humble background. I don’t have any intention to hart anyone’s sentiments and I respect each and every individual’s thoughts, religion, believes and faiths.
Thank you for reading so far. You are important for me, please leave your footprint here:
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-2754967439384345"
crossorigin="anonymous"></script>Types of Internet of Things (IoT)

The main objective of Internet of Things (IoT) is
- To globally connect smart ‘things’ or ‘objects’.
- Objects are uniquely identified.
- Interoperability among the objects.
These concepts are well explained in ‘Introduction to Internet of Things’.
Internet of things (IoT) is categorized in 3 segments:
- Industrial IoT (IIOT)
- Consumer IoT (CIOT)
- Enterprise IoT (EIOT).
In 5G Americas white paper 5G-The future of IOT it is mentioning that types of IoT use cases is not so much based upon the ‘who’ or ‘where’ but the requirements for the technology implemented.
This means the segmentation is not based upon what are the equipment, devices used in the system.
Same sensors, same actuators, and all other devices may be same in all 3 cases.
The devices used in home, in office, in a factory have the same functionalities.
But segmentation is done based on requirement of features of IoT connectivity in each sectors.
Mainly these 3 categories are done based on the below requirements:
- Security
- Interoperability
- Scalability
- Precision and Accuracy
- Programmability
- Low Latency
- Reliability
- Resiliency
- Automation
- Serviceability
- Data volume
- Data throughput
Some of these characteristics we have discussed in Introduction to Internet of Things (IoT).
Security is a major concern in all three categories.
In some scenario we may require very low latency and low data throughput. In some other cases we may compromise latency up to some level, but data uses or requirement of data throughput is very high.

Get YOUR Copy HERE.
1.Industrial Internet of Things (IIoT):
The industrial Internet of Things (IIot) is an application of IoT in industries to modify the various existing industrial systems.IIoT links the automation system with enterprise, planning and product life cycle.
IIoT includes major industries like:
- Oil and Gas,
- Transportation,
- Manufacturing,
- Healthcare and Energy.
Accenture forecast that the Industrial IoT will reach $123 billion in 2021, attaining a CAGR of 7.3 percent through 2020(Ibid). Accenture also forecast that IIoT can add as much as $14.2 trillion to the global economy by 2030 (Ibid)
Component of IIoT:
Some integral component of Industrial IoT (IIoT) are
- Machine Learning
- Big data technology
- Machine to Machine interaction (M2M)
- Automation
Machine Learning-
Learning from the existing data and trying to make things predictive and trying to have things which are better in the future, based on current available data.
Big data technology-
Big data means very big is size which ca not be processed with usual tools.
Big data is mainly based on 3 Vs. Those are
V- Volume of data: e.g. 500 TB per day (like in Facebook).
V- Velocity of data: e.g. trying to handle many requests per seconds (like in Google)
V-Variety of data: e.g. Problem at hand and data we will process are complex.
Machine to Machine interaction (M2M)& Automation-
Two or more machines directly interact with one another to complete some purpose or task without any human interventions.
Thus make the things possible to work in automation.
Industrial IoT (IIoT) and Industry 4.0:

The scope of Industry IoT (IIoT) borrows some features of IoT and borrows some features from vision of Industry 4.0.
Industry 4.0 is basically a framework for:
- Automation and data exchange in manufacturing technologies.
- Cyber-physical systems, Internet of things and cloud computing.
- Smart factory.
2.Enterprise IoT (EIoT):
The ultimate need for enterprise to drive IoT is to enhance:
- Operational efficiency,
- Mitigate risk,
- Improve functional visibility,
- Ensure maximum customer engagement,
- Increases revenue streams,
- And tap into potential opportunities for growth.
For connectivity purpose-
The 5G network is capable of supporting massive devices and new services, for example
- Enhanced Mobile Broadband (eMBB),
- Massive Machine type communication (mMTC),
- Critical communications and network operations
compared to 4G-LTE network.
5G mobile system for Enterprise IoT is trusted to provide low latency, high versatility and high throughput for large number of gadgets
Use cases:
Enterprise IoT would have the greatest impact in
- Service Operations
- Manufacturing.
These two broad groups can be further distributed into:
- Supply Chain
- Research & Development (R&D)
- Marketing and Sales
- And small segment of other parts of enterprise.
For example, manufacturing machines at the manufacturing floors are integrated with
- Enterprise resource planning (ERP),
- Customer relationship management (CRM),
- Supply chain management (SCM),
- And knowledge management (KM) applications in order to ensure utmost automation.
The results and outputs are simply the aggregated ones. Any event information gets instantaneously captured and processed in order to activate appropriate systems in time.
Any slight delay may lead to destruction. The much needed integration gets fulfilled through a host of integrators, connectors, drivers, and adaptors.
Key Drivers for Enterprise IoT:
The Enterprise IoT (EIoT) is relatively new development in the IoT sector.
Key drivers of Enterprise IoT (EIoT) are, but not limited to:
- Infrastructure optimization
- Process excellence
- Architecture assimilation
- Technology adaption and adoption
- Leverage data (internal as well as external) toward actionable insights
3.Consumer IoT (CIoT):
The IoT is changing how consumers interact with consumer electronics, enabling greater convenience for a better experience, access to data that enables them to optimize their usage, and increasing control they have over their devices.
With IoT, the world is at our fingertips.
Wearables,gadgets and gizmos, portables, implantable, handhelds, consoles, appliances, instruments, and utensils are the fast-emerging and evolving IoT products.
The number of connected devices in the hands of people in our everyday works and walks are drastically increasing.
Use cases:
- Fitness tracker,
- Smart home thermostat,
- Wi-Fi connected camera,
- Virtual reality headset,
- smart refrigerator and toaster,
- Alarm panel
- Smart glasses.
The connection between all of them is that they are often controlled by apps.
Growth of Consumer IoT (CIoT):
Consumer IoT is no more in the study state. These are already in our used cases and it is very fast growing sector of IoT.
For example, as per Statista The North America IoT consumer electronics market is predicted to increase from $90B in 2017 to $180B in 2022, attaining a CAGR of 12.25 percent.
Summary:
In this article we just touched all the categories of Internet of Things (IoT) to give a brief idea.
We will go deep in to all segments in upcoming blogs.
Thanks for reading this blog.
Your feedback, comments, suggestions or like are highly appreciated.
Ref:
5G Americas: 5G-The Future of IoT
The Internet of Things- by Pethuru Raj &Anupama C. Raman
Introduction to IoT- by Dr. Sudip Misra

Get YOUR Copy HERE.

Pranab Hazarika
BE | MBA | PMP | IoT-Certified
www.PranabHazarika.com
Transmission Microwave Backhaul Optimization in Telecom Network

In telecom network Transmission backhaul is the main Backbone of the network.
Whatever technology we may use 2G, 3G, LTE or even 5G the main support provided by transmission network only and desired data speed can only be obtained if we have sufficient available bandwidth in transmission links.
These transmission links may be:
- Microwave
- Fibre
- VSAT
- Or any other medium.
In telecom network first three types of transmission medium is mainly used.
VSAT is only used in cases where the target location is very remote and Line of Sight (LOS) is not cleared anyhow.
Additionally installation as well as maintenance cost of VSAT is very high. And available bandwidth is low. So expected bandwidth are usually 512 Kbps or somewhat nearby.
So main transmission medium till 3G network was only Microwave though fibre was preferred for redundancy, path protection and main backhaul connectivity.
When 4G came, fibre become a part and parcel of the network as to get desired data speed of 4G. We need huge bandwidth to support 4G speed.
In 4G it is a combination of Fibre as well as Microwave connectivity.
When 5G will come up as a normal service fibre will play the main role of connectivity.
Transmission Bandwidth Requirement:
Per site bandwidth requirement based on technology wise and spectrum wise are as below:

TDD & MM coexistence site:
For a site where TDD and MM (Massive MIMO) both are present then bandwidth of MM is considered as the bandwidth of the site.
TDD bandwidth for that particular site is not added to the MM bandwidth.
More than 1 sector MM site:
For more than 1 sector MM (Massive MIMO) site, total bandwidth of the site is considered as:
Site BW= MM Bandwidth of 1 sector * 1.5
We can take the below examples:
Let’s take 20 MHz bandwidth scenario for both MM and TDD
Site with 1 MM sector + 2 TDD sectors:
Site bandwidth will be 200 Mbps.
Site with 2 MM sectors+ 1 TDD sector:
Site bandwidth will be 300 Mbps.
i.e 200 Mbps of 1 sector of the MM * 1.5 times.
Site with 3 MM sectors:
Site bandwidth will be 300 Mbps.
i.e 200 Mbps of 1 sector of the MM * 1.5 times
Massive MIMO sites required very high backhaul requirement.
So these sites are ideally planned in fibre pop locations only.
Here we should not be confused with bandwidth of Radio frequency planning and transmission bandwidth.
Here we are discussing only about transmission/backhaul bandwidth. About Radio Frequency bandwidth we discussed in “Voice and Data Capacity Calculation of 2G, 3G and LTE Network”.
Now we can understand that based on backhaul available bandwidth we can expect data speed on our mobile. Speed is also depends on Technology i.e. 3G, 4G or 5G and their modulation scheme.
If congestion occurs in transmission network, data speed gets reduced.
These congestion are mainly happens in case of data linked sites i.e. 3G or 4G sites.
So it is very much required to check and do optimization of the transmission links.
If utilization of a transmission link goes beyond 70% then we should plan to optimize or upgrade the links.
There are mainly 3 different methods we can apply to upgrade or optimize a link.
- Bandwidth up-gradation
- Link re-routing
- Link equipment up-gradation.
Bandwidth up-gradation:
For IP nodes we can upgrade the available bandwidth of the microwave links.
Suppose a link is working on available bandwidth of 183 Mbps then we can upgrade it to 214 or 240 Mbps and check if the link utilization is going down or not.
If some links are working below 183 Mbps, then we can upgrade those links to 183 Mbps.
Only problem in upgradation of bandwidth is that with new bandwidth if we run link budget in some cases it may shows loss of availability of the link.
If this problem occurs then we should not prefer bandwidth upgradation.
This problem occurs because, with bandwidth increase we have to also increase power.
If power is already in maximum, then this may give a low receive level at the receiver end.
Advantageofbandwidth upgradation is that no additional cost involved and less time consuming. If link budget in planning tool works perfect then we can immediately implement the same in the system.
Link re-route Engineering:
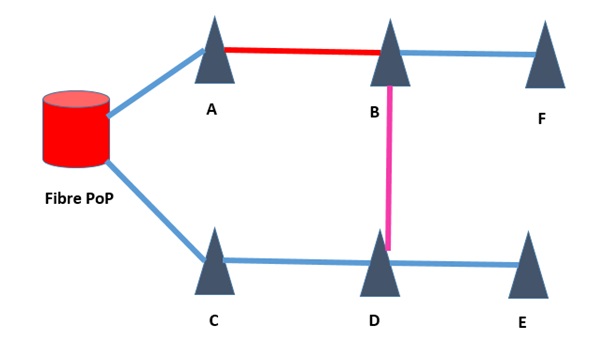
We take an example of the above figure as a part of our network.
In the above figure “A” to “F” are Base stations (BTS). Serving route of F is in the direction from Fiber pop up to BTS location “F”. The physical route of serving E1 is “Fibre PoP-A-B-F”.
Link “A-B”is congested and bandwidth upgradation can’t be done. This link is carried traffic of nodeB (3G)/enodeB(4G) “B” as well as nodeB(3G)/enodeB(4G) “F”.
Remaining all other links are not highly utilized.
So if we reroute path of “F” then congestion level may goes down in the link between “A-B”.
Here we can make a new route in the direction “Fibre PoP-C-D-B-F”.
This is a very simple case we are considering here for ease of understanding.
Main issue in such type of activity is that once we route “F” through new route “Fibre PoP-C-D-B-F” there may be chances that any link of this route may get congested.
So, for that, before making a new route we have to check each link of the new route whether they are able to handle new traffic of “F” or not.
If not then there is no meaning of doing of all these rerouting activities and plan for some other alternatives.
Link equipment up-gradation
Third option is link equipment upgradation.
We can replace the MW hop with XPIC (Cross Polarization) hop.
This will double the capacity of the link.
If the congested link is already a XPIC hop then we may plan for some new fibre PoP.
XPIC upgradation and Fibre PoP plan both have cost involvement.
So this is the last option we choose if all other possibilities failed.
Summary:
Once we have noticed any link utilization greater than 70% we plan for any of the three methods that we discussed above.
Transmission Link should have enough available bandwidth in 3G, 4G and 5G network to get desired data speed.
Thanks for reading this blog.
Your feedback, comments, suggestions or like are highly appreciated.

Pranabjyoti Hazarika
BE | MBA | PMP | IoT-Certified
Introduction to Internet of Things (IoT)
A formal definition of Internet of Things is as below:
“”The Internet of Things (IoT) is the network of physical objects that contain embedded technology to communicate and sense or interact with their internal states or the external environment.””
Now let’s understand Internet of Things in very simple way.
Till now when we say internet based services we understand connections of different computers and computing devices.
Now the Internet of Things says that the scope of internet is expanded or going to be expanded beyond computers and computing devices.
Now whatever “things” we can see, we can touch can be a part of the internet of world.
They will communicate in between, with humans and so on.
So in simple terms anything can be connected to the internet world and this is called Internet of Things (IoT).
IoT is no more in research state and by 2020 it is expected that 50 billion devices will be part of IoT.
This count will increase gradually as the use of devices, equipment, home appliances are increasing day by day and they are always more than human beings.

Get your copy here
Application of Internet of Things (IoT):
Some applications of Internet of Things in different domains are as below but not limited to:
- Home: Smart Lighting, Smart Appliances
- Cities: Smart Parking, Smart Roads
- Environment: Weather Monitoring, Noise Pollution Monitoring
- Energy: Smart Grids, Renewable Energy System
- Retail: Inventory Management, Smart Payments
- Logistics: Shipment Monitoring, Route Generation
- Agriculture: Smart Irrigation, Green House Control
- Industry: Indoor Air Quality Monitoring, Machine Diagnosis
- Health & Lifestyle: Fitness Monitoring, Wearable Electronics
Market Drivers of Internet of Things (IoT):
IoT is a new game changer for businesses and individuals and is considered to be the fourth industrial revolution by experts and scientists.
The drivers and trends that contribute to the massive growth and development of IoT are as below, but not limited to:
- 3GPP standards
- Expanded and low cost internet connectivity
- Expanded mobile communication
- Emerging of new mobile technology like LTE and 5G.
- Low cost sensors
- Large IoT investments
- Growing importance of Automation
- Big data knowledge
- Artificial Intelligence
- Machine learning
- Deep learning
- Edge computing and cloud
- Security assistance
- IPV6 addressing system
Characteristics:
Different characteristics of IoT are:
- Efficient, scalable and associated architecture
- Unambiguous naming and addressing
- Abundance of sleeping nodes, mobile nodes.
- Intermittent connectivity
- As we already came to know that in IoT billions of, trillions of devices are going to be interconnected so, it must be scalable and as well as efficient too.
- Identification of each nodes must be unique. Currently IPV4 system is usually used for IP addressing which is having 32 bit addressing scheme.
For IoT we need to think beyond IPV4 and necessity to go for IPV6. IPV6 is having 128 bit addressing scheme.
- There should be large number of sleeping nodes in the system.
Whenever they are not being used they should be in sleeping mode and as per requirement make them active.
As there are large no of nodes connected in the network it is not possible to check and change battery or power supply to the nodes very frequently.
So the battery life of the nodes should be very large like many years. To make the battery life long, we should make some arrangement so that all nodes are continuously not active and go to sleep mode when they are not required to be active.
By this way we can make long battery life of the nodes and thus make them long live.
- Mobility of the nodes is also a part of IoT network.
e.g. if a person is wearing a smart watch, along with the person that nodes must also be mobile and should work properly during mobility.
- Intermittent Connectivity means one device currently connected to a particular device may not be connected to it at a later instance of time and gets connected to some other new device or devices.
IoT Market Share:
IoT is attractive in different application domains.
A study found that currently the IoT market share in different domains are like (Source: Intel)
Manufacturing/ Business: 40.2%
Healthcare: 30.3%
Retail: 8.3%
Security: 7.7%.
So we have seen that currently Manufacturing /Business is on the top of the IoT market share.
It improves overall supply chain management, different sensors, actuators, different robotic machinery can be used to improve the business process.
In healthcare remote areas can be connected to the different health care facilities of doctors, nurses, and other services whether they are present in front of them or not.
They will be remotely connected and treated.
Recordkeeping and access remotely to those reports is also an added advantages to healthcare industry.
In case of Retail sectors tasks such as inventory tracking, smartphone purchasing, anonymous analytics of consumer choices, these are the different things that can be done efficiently through use of IoT.
Fingerprint, biometric and facial recognition these technologies can be connected and used with the help of IoT for Security purpose.
Machine to Machine (M2M) Communications:
Machine to Machine (M2M) communications was first introduced by Telecommunications service providers (TSP).
Earlier IoT was referred to as Machine to Machine (M2M) communications only.
M2M means devices connected to internet can communicate to one another through wired and mostly wireless network.
From this concept of M2M with evolved communication technology like 4G-LTE or 5G, concept of MASSIVE IoT deployment comes in to picture.
Along with Massive another part of IoT is CRITICAL IoT.
Massive IoT:
Requirements of Massive IoT:
- Low cost
- Low energy
- Small data volumes
- and Massive numbers of devices.
Examples are like smart buildings, smart agriculture, logistic tracking and management etc.
Critical IoT:
Requirements of CriticalIoT:
- Ultra-Reliable
- Very low latency
- Very high reliability
Examples are like remote health care, traffic safety and control, industrial applications and control etc.
M2M expansion is growing in very high speed and Cisco predicting that by 2022 there will be 14.6 billion machine-to machine (M2M) IoT connections.
IoT Vs M2M:
M2M refers to the communications between machines and devices.
Internet of Things (IoT) is a wider concept and M2M is a part of IoT, reverse is not.
Expectation of IoT:
Applications of IoT can be expected in almost every sphere of society and any sphere of life.
It is expected to have trillions of sensors (nodes), billions of smart systems and millions of applications are going to be internetworked.
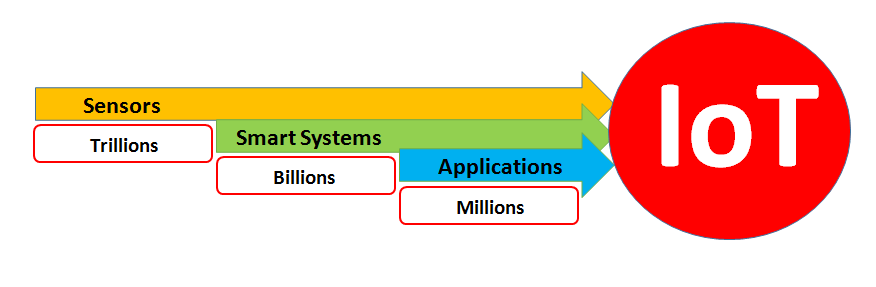
Summary:
This is just a beginning of the Internet of Things (IoT) chapter.
In upcoming blogs we will go deep in to the concepts, theory, devices and applications of IoT in details.
Thanks for reading this blog.
Your feedback, comments, suggestions or like are highly appreciated.
Ref: Internet of Things, A Hands-on approach by Arshdeep Bahga& Vijay Madiset
5G the future of IoT, 5G Americas
Internet of Things: Dr. Sudip Misra



Pranab Hazarika
BE | MBA | PMP | IoT-Certified